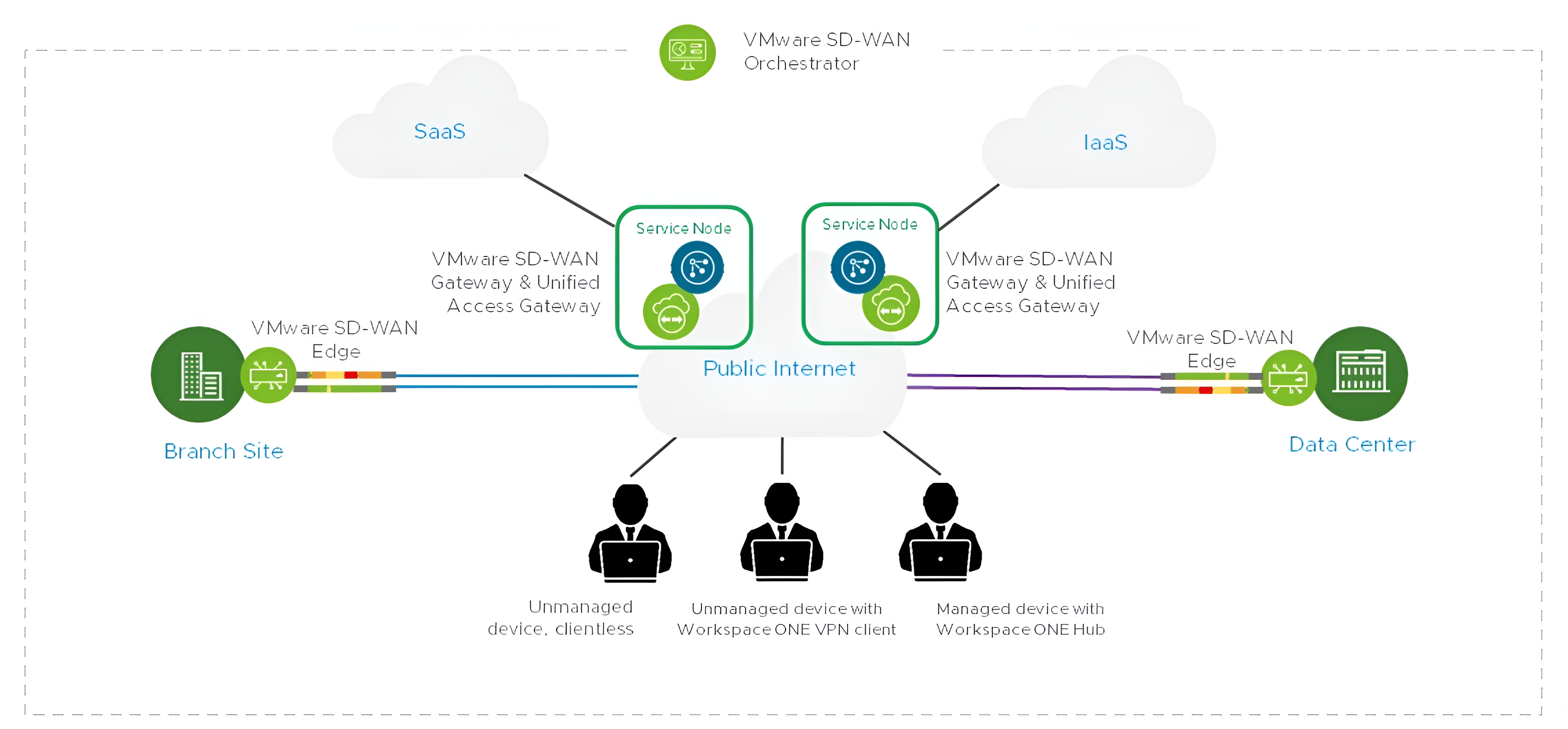
Zero Trust Network Access (ZTNA)
In an era of increasingly sophisticated cyber threats and distributed workforces, traditional perimeter-based security models are no longer sufficient. Our Zero Trust Network Access (ZTNA) solution provides robust, identity-driven security to protect your organization’s resources, no matter where your employees, devices, or applications are located. Trust no one, verify everything—this is the foundation of our Zero Trust approach.

Why Choose Our Zero Trust Network Access (ZTNA)?
In today’s increasingly mobile and cloud-based world, Zero Trust Network Access (ZTNA) is essential for ensuring your network’s security. By verifying identity, devices, and user context at every access point, you significantly reduce the risks associated with remote work, unauthorized access, and security breaches. Protect your applications, data, and resources while enabling a more flexible, secure working environment.
Real-Time Monitoring & Analytics
Gain actionable insights into user behavior, access patterns, and potential security risks across your organization.
Identity-First Security Model
With ZTNA, access to your network is granted based on identity and device trust, not on location or network perimeter. This means that only authenticated and authorized users and devices can access specific resources, ensuring tighter security for your business-critical applications.
Continuous Verification & Least-Privilege Access
ZTNA operates on the principle of least-privilege access, continuously verifying the trustworthiness of both users and devices. This minimizes the attack surface by ensuring users only have access to the specific resources they need—no more, no less.
Secure Remote Access for a Distributed Workforce
Whether employees are working remotely, from branch offices, or on the go, ZTNA ensures secure access to applications without the need for complex VPN solutions. Employees can securely access resources from any device, anywhere, without compromising security.
Simplified User Experience
Our ZTNA solution provides seamless and frictionless access for end-users while enforcing strong security policies. Users can easily access the resources they need without the cumbersome authentication challenges typical of traditional security methods.